Why is software-defined networking a target, and what are the different tactics organizations can deploy to keep the network secure?
Your Network at Risk
What is SD-WAN architecture?
A software-defined wide area network (SD-WAN) is a virtual WAN architecture connecting hardware at different locations. Through the use of SD-WAN, users can transport data through various types of connections such as private lines, multiprotocol label switching (MPLS), virtual private networks (VPN), LTE, and broadband internet. In contrast to the traditional WAN model, SD-WAN enables data to be transferred directly between locations (or along the most efficient path) without passing through a consolidated, central data center. By eliminating the need for the centralized data center, SD-WAN promotes increased efficiency of data transference, lowers latency, and, notably, enables users to monitor the flow of data and measure performance indicators. However, though the traditional WAN architecture is less efficient due to the longer distance traveled by the data, there are additional security risks associated with a shift to SD-WAN.
Why Is SD-WAN A Target?
Because SD-WAN does not require that data pass through a centralized data center en route to its ultimate destination, the implementation of certain security protocols is complicated. Specifically, when data is permitted to move between locations without being passed through the security appliances – firewall, IDS/IPS, DLP, etc. – security risks and vulnerabilities are introduced at every point of data transference and attacks are not blocked or prevented at the centralized data center as they are in the traditional WAN model. Additionally, security risks and vulnerabilities can be introduced if security configurations at these various locations are inconsistent with one another. Though it is less efficient, the centralization of data with a traditional WAN means that there are fewer possible points of vulnerability from a security standpoint. SD-WAN outpaces the traditional model and is continuing to overtake it in popularity, but its more numerous and complex vulnerabilities make it a distinctive target for attackers and ensure that stronger security measures are taken than have previously been needed.
How to Protect Your Data
Because a centralized data center does not do the work of protecting transferred data in the SD-WAN model as it does in the traditional WAN model, the security of your data can only be ensured by establishing the necessary security protocols at all locations. Because of the advanced capabilities of SD-WAN, however, users are given more options to protect their data than ever before. When proper security measures are taken, SD-WAN enables users to exert more control over their data and the measures taken to secure it by directing traffic only where it needs to go and allowing internal security policies to govern its movement on a smaller, more individualized level.
Different Ways to Keep Your Network Secure
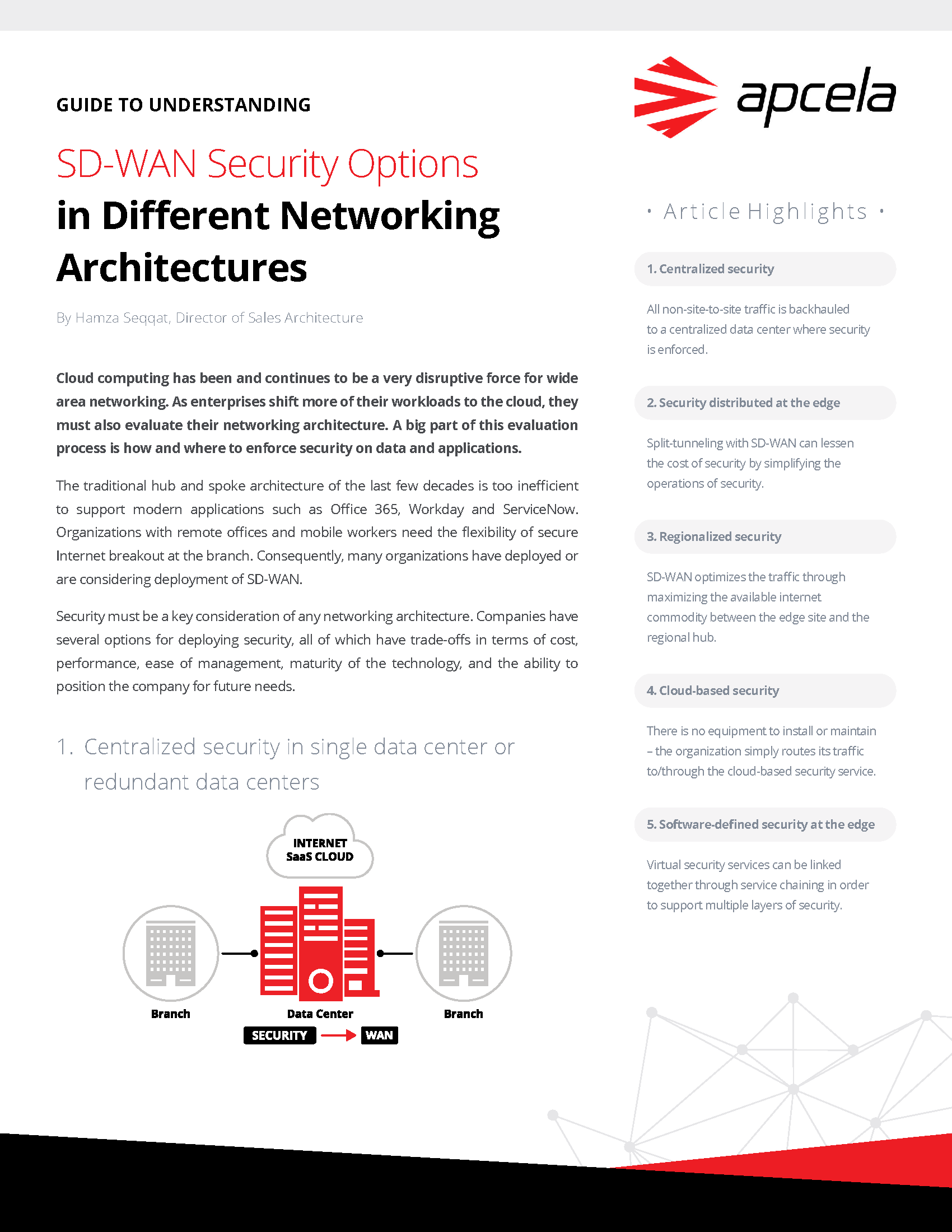
Centralized Security in a Single Data Center
This method of network security is the one most commonly associated with the traditional WAN architecture. With this option, all off-site traffic is backhauled from its point of origin to a physical, central data center before being directed to its ultimate destination. Though this option has certain advantages over the more modernized approaches given its more consolidated nature and consequently fewer points of security vulnerability, the performance discrepancies between a physical approach like this one and a more software-defined approach which allows for the direct transference of data are increasingly limiting its modern relevance.
Software-Defined Security at the Edge
According to this option, security is ensured at all locations through the implementation of security delivered as software (i.e. Virtual Network Functions, or VNFs) at the network boundaries of each branch location. This approach allows locations to exchange data and internet traffic at the edge without having to backhaul it to the centralized data center. While this method provides a significant advantage over the previous one in terms of increased efficiency and latency reduction, it comes with the challenge of consistently securing all locations individually which can be costly and potentially dangerous from a security standpoint. However, the cost associated with this method is minimized by the avoidance of expensive hardware appliances through the software-defined approach. Additionally, the software-defined approach allows for easier management of security protocols either from within the organizations data management center or by a managed services provider.
Apcela’s Recommendations
SASE is the way to go
Apcela promotes the use of a Secure Access Service Edge (SASE) approach to network security. SASE is the combination of SD-WAN capabilities with security services delivered through a cloud-based delivery model. Through SASE, users can take a personalized approach to their network management and security. It provides the user with highly customizable, policy-based control over their performance and security that can be tailored by user identity, session context, and application needs for performance and security.
Don’t forget about the Cloud
Further, Apcela recommends the implementation of a multi-cloud strategy in combination with SASE and SD-WAN for maximized security and optimization. Through the use of a multi-cloud strategy, users can select the cloud services that best suit their individual needs. This strategy, combined with the SASE approach, promotes a generally improved user experience and reduces redundancy. The trend away from physical hardware and data centers towards a software-defined, multi-cloud approach empowers users to take control of their networking experience and security. To learn more about how Apcela can help you adopt a software-defined approach to network security, read about our Arcus Platform here.